Wednesday, December 30, 2009
Open source voting machines—an opportunity for Hawaii
by Larry Geller
Hawaii could save money, create jobs, recycle many old computers, and protect the integrity of its vote by choosing to participate in an open-source voting project. I’ve mentioned this before, but this time there are details.
 Open source voting is real. It doesn’t take a Diebold or other commercial company to produce a workable, secure voting system.
Open source voting is real. It doesn’t take a Diebold or other commercial company to produce a workable, secure voting system.
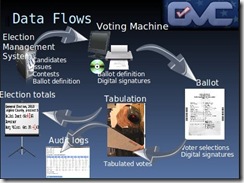
Have a look at the Open Voting Consortium web pages and view their slide presentation. The slides show how a complete voting system might work.
Also check out the Open Source Digital Voting Foundation and its Trust the Vote Project.
The TTV project is a digital public works project, creating freely available, non-proprietary technology that is maintained as a public trust. Open source technology and practices are a key aspect of a public works project, and a critical ingredient in the TTV recipe for creating public trust in election technology, via technologically enabled transparency.
But first, we need to look at the security issue with commercial voting systems. It’s not just “vote flipping,” which has been demonstrated. Secret computer code means that sophisticated manipulation is possible and may go undetected.
“Man in the Middle” attacks—what are they?
If you live on a Neighbor Island, your vote, after the polls close on an election day, has to somehow get to Oahu. As an avid web surfer, you know that on the Internet anything goes, and that danger lurks in every electronic nook and cranny. Why would you trust the Internet to safely carry your vote to Oahu? Or if a voting machine dials, do you know who it is calling?
The problem is really “chain of custody.” To protect your vote, someone has to be responsible for it at every point along the way, with no breach of custody. When votes are accumulated and then sent by a commercial voting machine to a counting center, no one knows what number the machine is really dialing. It could be someplace in between where the votes are altered and then sent on to Oahu in minutes. No one would know. This is the famous “man in the middle” attack.
The software in these commercial machines is written by unknown persons, and there is no assurance it’s the same as the software in the voting machine you use anyway. It’s proprietary. You can’t see it. You can’t check it. You don’t know what’s driving the voting computer that you use at the polling place, or the machines used to accumulate and forward votes to Oahu.
This concern lead Bob Babson, lead plaintiff in Babson v. Cronin, to file his lawsuit. Babson prevailed. In order to fix things with the court, the Office of Elections has had to write new administrative rules covering electronic voting. Until those rules come into effect, a judge’s order prevents Hawaii from completing the procurement process for voting machines.
According to testimony that Babson submitted for the public hearing on the proposed administrative rules, the new rules won’t protect the vote. His testimony is posted at the bottom of this article.
Open source voting may solve the problem
 Last weekend I played with my very own voting machine—on my own computer. It was a CD that I can load and which boots up its own little operating system and voting environment, complete with a sample ballot. Because the code is entirely on a CD, it can’t be altered. The computer that runs it for an actual election doesn’t need (and shouldn’t have) a hard disk or USB ports.
Last weekend I played with my very own voting machine—on my own computer. It was a CD that I can load and which boots up its own little operating system and voting environment, complete with a sample ballot. Because the code is entirely on a CD, it can’t be altered. The computer that runs it for an actual election doesn’t need (and shouldn’t have) a hard disk or USB ports.
I can also look at the code myself—it’s open source! Everyone can look at the code.
This solves the “man in the middle” problem because the only thing that the machine can do is what’s programmed on that CD. If the CDs are serialized and kept securely, they cannot dial any strange numbers or send anything to a funny place on the Internet.
Would you like to try your own prototype open-source voting machine? You can boot the disk or geeks can run it in a virtual machine (for example, I ran mine in VMPlayer, a free program).
Get your disk (it’s called a LiveCD) at the SHARP Project page. Vote with your mouse.
How does open-source voting work?
First, it’s secure. The disks are serialized and sent to the precincts in sealed bags. If there is any doubt about a disk, it is open-source. It can be compared with another disk, or someone could even read the code and check it by hand.
It’s not too well known, but there are also ways to authenticate a disk using encryption codes.
Any configuration can be open-source. My favorite is this: each machine has a printer to print out a paper ballot. It could be any kind of printer as long as it works (has ink, paper feeds straight, etc.). It could be new or used, expensive or cheap. It prints your paper ballot after you use the machine. Yup, a paper ballot you can verify.
 The ballots can be read as now by scanners (open source code, of course) or with hand-held scanners of the type you see in supermarkets (as is being done in the slide at the left, part of the OVC slide presentation).
The ballots can be read as now by scanners (open source code, of course) or with hand-held scanners of the type you see in supermarkets (as is being done in the slide at the left, part of the OVC slide presentation).
The software can present multiple languages on the screen or print ballots in any language for verification.
This is so good, we should do it. With the Office of Elections almost paralyzed by the administration’s 94% budget cut, legal challenges and the resignation of Hawaii’s Chief Election Officer, it won’t happen for the 2010 election. But why spend $2.8 million to profit a commercial company when part of that money could go towards local development of open source voting software we can use on into the future?
Finally, any old computer works fine for this application. Let’s collect some of those ancient Windows 98 clunkers, yank out the hard disks, and recycle them into voting machines.
Ok, ‘nuff said, here’s Bob Babson’s testimony on the flaws in the proposed administrative rules for electronic voting.


Post a Comment
Requiring those Captcha codes at least temporarily, in the hopes that it quells the flood of comment spam I've been receiving.